Sunday, March 1, 2020
what is live scribe pen ?
The Live scribe paper based computing platform consists of a digital pen, digital paper, software applications and developer tools. Central to the LIvescribe platform is the smartpen, a ballpoint pen with an embedded computer and digital audio recorder. When used with Anoto digital paper, it records what it writes for later uploading to a computer, and synchronizes those notes with any audio it has recorded.
Friday, January 31, 2020
WHAT IS SIMAS BATTERY ?
- A web based educational computer system simulator, conveniently named SIMAS is described in this paper. The simulater uses animation and visualization to express the process of machine code execution. The software package enables the user to enter an assembly language program and to compile it.
- synchronizes the operations of other elements of the system.
- The control unit performs these functions by repeatedly fetching program instructions from the memory and decoding them. Based on the decoded type of the instruction, it then generates corresponding control signals to execute the instructions.
- During the system operation the cpu communicates with the main memory, which stores program data and instructions.
WHAT IS JOYSTICK ?
In computers, a joystick is a cursor control device used in computer games and assistive technology. The Joystick, which got its name from the control stick used by a pilot to control the ailerons and elevators of an airplane, is a hand-held lever that pivots on one end and transmits its coordinates to a computer.
WHAT IS DVD ?
DVD means digital versatile disk. Is a digital optical disc storage format invented and developed in 1995 and released in late 1996. The medium can store any kind of digital data and is widely used for software and other computer files as well as video programs watched using DVD players. A type of optical disk technology similar to the CD-ROM. A DVD holds a minimum of 4.7GB of data, enough for a full-length.
WHAT IS CD ?
CD means compact disc. Is a digital optical disc data storage format that was co-developed by philips and Sony and released in 1982. The format was originally developed to store and play only sound recordings (CD-DA) but was later adapted for storage of data (CD-ROM). A compact Disc, also called a CD are small plastic discs which store and retrieve computer data or music using light.
Abbreviated as CD, a compact disc is a flat, round, optical storage medium invented by James Russell.
WHAT IS COMPUTER SOUND CARD ?
A sound card is an expansion card or IC for producing sound on a computer that can be heard through speakers or headphones. Although the computer does not nead a sound device to function, they are included on every machine in one form or another, either in an expansion slot or built into the mother board.
WHAT IS JUMPER ?
In electronics and particularly computing a jumper is a short length of conducter used to close, open or bypass part of an electronic circuit. They are typically used to set up or configure printed circuit boards, such as the mother boards of computers. The process of setting a jumper is often called strapping.
WHAT IS IC PROCESSOR ?
A CPU is an internal processing unit of circuitry that interprets and carries out computer programming. An IC is a set of circuits constructed on a single semiconductor wafer or chip, in which the components are inter connected to perform a given function.
A microprocessor is an integrated circuit which incorporates core functions of a computer's central processing unit. It is a programmable multipurpose silicon chip, clock driven, register based, accepts binary data as input and provides ouptut after processing it as per the instructions stored in the memory.
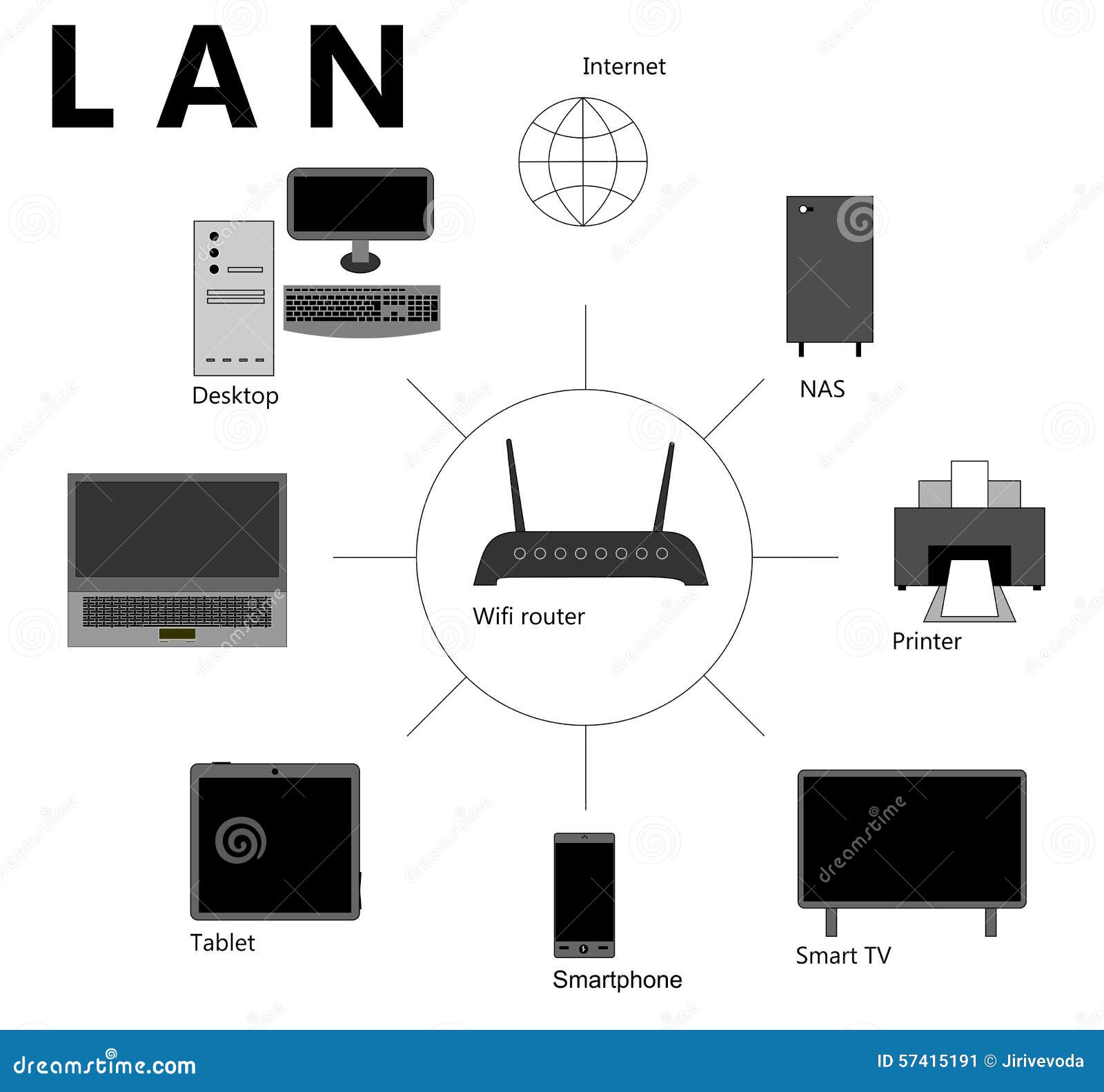
WHAT IS LAN ?
WHAT IS HEAT SINK ? AND HEAT SINK ON THE PROCESSOR ?
A heat sink (also commonly spelled heatsink) is a passive heat exchanger that transfers the heat generated by an electronic or a mechanical device to a fluid medium, often air or a liquid coolant, where it is dissipated away from the device, there by allowing regulation of the device's temperature at optimal levels. In computers, heat sinks are used to cool CPUs, GPUs, and some chipsets and RAM modules.
WHAT IS USB ? AND AUDIO SOUND CARD ?
External USB audio cards give a user better sound quality and results than a standard, on board sound card, in terms of performance. Usually external cards can provide better bit depth while recording. If you have never before tried using an external USB sound card, you may have a few questions as to getting it properly set up and configured on your machine. With the right instruction, you too can make most out of your new audio device.
WHAT IS ARTIFICIAL INTELLIGENCE ?
In computer science, artificial intelligence , sometimes called machine intelligence, is intelligence demonstrated by machines, in contrast to the natural intelligence displayed by humans. Leading AI text books define the field as the study of " intelligent agents". any device that perceives its environment and takes actions that maximize its chance of successfully achieving its goals.
Colloquially, the term "artificial intelligence" is often used to describe machines ( or computers) that mimic " cognitive functions that humans associate with the human mind, such as " learning " and " problem solving.
As machines become increasingly capable, tasks considered to require " intelligence " are often removed from the definition of AI, a phenomenon known as the AI effect hasn't been done yet. For instance, optical character recognition is frequently excluded from things considered to be AI, having become a routine technology. Modern machine capabilities generally classified as AI include successfully understanding human speech, competing at the highest level in strategic game systems.
what is 5th Generation of artificial Intelligence ?
The fifth generation computer systems was an initiative by japan's Ministry of international Trade and Industry begun in 1982, to create computers using massively parallel computing and logic programming. It was to be the result of a massive government/ industry research project in Japan during the 1980s.
Monday, January 27, 2020
WHAT IS HISTORY OF HTML ?
IBM SOWED THE SEED OF HTML in the early 198/0s. Initially, it was known as GML (General Markuup language). It was a powerful tool that aime at creating a documentation language in which one could mark the title, headigs, text,font selection and how much more. In 1986, this concept got standardized by ISO and was named SGML (Standard Generalized Marku-up language). In 1989,Tim Berners Lee and his team designed this language and named it as HTML (Hyper text markup language). The language HTML was modified many times leading to a number of versions i.e., HTML version 0 to version 5 which is the latest one.
HTML: It stands for Hyper Text Mark-up Language. HTML is a complete code package that allows the user to create web pages. It includes text and graphics. Using HTML, we can add links to the web pages. Hyper links are the highlighted text segments or images that connect to other pages on the web. Let us analyze the word HTML.
HYPER TEXT: Hyper text is the text used to link various web pages. It is the text on a web page, which on clicking opens a new web page.
MARK-UP: It means highlighting the text either by underlining or displaying it in different colors, or both.
LANGUAGE: It refers to the way of communication between web pages, which has its own syntax and rules.
HTML: It stands for Hyper Text Mark-up Language. HTML is a complete code package that allows the user to create web pages. It includes text and graphics. Using HTML, we can add links to the web pages. Hyper links are the highlighted text segments or images that connect to other pages on the web. Let us analyze the word HTML.
HYPER TEXT: Hyper text is the text used to link various web pages. It is the text on a web page, which on clicking opens a new web page.
MARK-UP: It means highlighting the text either by underlining or displaying it in different colors, or both.
LANGUAGE: It refers to the way of communication between web pages, which has its own syntax and rules.
Tuesday, January 21, 2020
WHAT IS STAR NETWORK TOPOLOGY ? ADVANTAGES AND DISADVANTAGES ?
Alternatively referred to as a star network, star topology is one of the most common network setups. In this configuration, every node connects to a central network device, like a hub, switch, or computer. The central network device acts as a server and the peripheral devices act as clients. Depending on the type of network card used in each computer of the star topology, a coaxial cable or an RJ-45 network cable is used to connect computers together. The image shows how this network setup gets its name, as it is shaped like a star.
Advantages of star topology
- Centralized management of the network, through the use of the central computer, hub, or switch.
- Easy to add another computer to the network.
- If one computer on the network fails, the rest of the network continues to function normally.
Disadvantages of star topology
- May have a higher cost to implement, especially when using a switch or router as the central network device.
- The central network device determines the performance and number of nodes the network can handle.
- If the central computer, hub, or switch fails, the entire network goes down and all computers are disconnected from the network.
WHAT IS TRANSISTERS ?
A transistor is a semiconductor device used to amplify or switch electronic signals and electrical power. It is composed of semiconductor material usually with at least three terminals for connection to an external circuit. A voltage or current applied to one pair of the transistor's terminals controls the current through another pair of terminals. Because the controlled (output) power can be higher than the controlling (input) power, a transistor can amplify a signal. Today, some transistors are packaged individually, but many more are found embedded in integrated circuits.
Austro-Hungarian physicist Julius Edgar Lilienfeld proposed the concept of a field-effect transistor in 1926, but it was not possible to actually construct a working device at that time.[1] The first working device to be built was a point-contact transistor invented in 1947 by American physicists John Bardeen and Walter Brattain while working under William Shockley at Bell Labs. They shared the 1956 Nobel Prize in Physics for their achievement.[2] The most widely used transistor is the MOSFET (metal–oxide–semiconductor field-effect transistor), also known as the MOS transistor, which was invented by Egyptian engineer Mohamed Atalla with Korean engineer Dawon Kahng at Bell Labs in 1959.[3][4][5] The MOSFET was the first truly compact transistor that could be miniaturised and mass-produced for a wide range of uses.[6]
Monday, January 20, 2020
WHAT IS HUB ?
HUB
Wheel components[edit]
- A hub is the central part of a wheel that connects the axle to the wheel itself.
- Bicycle hub, the central part of a bicycle wheel
- Locking hubs, accessory on four-wheel drive vehicles
- Wheel hub assembly, an automotive part
Arts and media[edit]
- Hub (comics), a Marvel comics fictional character
- The Hub (Torchwood), a setting in the television series Torchwood
- Hub Network, a digital cable and satellite television channel
Buildings[edit]
- The Hub (building), a residential skyscraper in Brooklyn, New York
- HUB Tower, in Des Moines, Iowa
- Husky Union Building, at the University of Washington
- Hubbard Hall, a residence hall at the University of New Hampshire
Computing[edit]
- Hub (network science), referring to a node with a huge number of links
- Email hub, a computer system dedicated to relay e-mail messages
- Hubs and authorities, a scheme used for ranking web pages
- USB hub
- Ethernet hub, a computer networking hardware device
- ARCNET hub
- SATA hub or port multiplier
Organizations[edit]
- Hub Culture, a social network company
- Harvard University Band
- Hogeschool-Universiteit Brussel, Belgium
- Hub International, a North American insurance brokerage
Places[edit]
Pakistan[edit]
- Hub, Balochistan, a city in Pakistan
- Hub Dam, in Balochistan, Pakistan
- Hub River, in Balochistan, Pakistan
- Hub Tehsil, in Balochistan, Pakistan
Elsewhere[edit]
- Hub, California, US
- Hub, Mississippi, US
- Boston, Massachusetts, US
- Hub City (disambiguation)
- Hubei, a province of China (Guobiao abbreviation HUB)
Transport[edit]
- Airline hub, an airport used as transfer point
- Transport hub, where traffic is exchanged across several modes of transport
- Hunmanby railway station, England
HOW TO CONNECT ROUTER TO COMPUTER ?
This article is about the network device. For the woodworking tool, see Router (woodworking).
A router[a] is a networking device that forwards data packets between computer networks. Routers perform the traffic directing functions on the Internet. Data sent through the internet, such as a web page or email, is in the form of data packets. A packet is typically forwarded from one router to another router through the networks that constitute an internetwork (e.g. the Internet) until it reaches its destination node.[2]
A router is connected to two or more data lines from different IP networks.[b] When a data packet comes in on one of the lines, the router reads the network address information in the packet header to determine the ultimate destination. Then, using information in its routing table or routing policy, it directs the packet to the next network on its journey.
The most familiar type of IP routers are home and small office routers that simply forward IP packets between the home computers and the Internet. An example of a router would be the owner's cable or DSL router, which connects to the Internet through an Internet service provider (ISP). More sophisticated routers, such as enterprise routers, connect large business or ISP networks up to the powerful core routers that forward data at high speed along the optical fiber lines of the Internet backbone.
Contents
Operation[edit]
When multiple routers are used in interconnected networks, the routers can exchange information about destination addresses using a routing protocol. Each router builds up a routing table listing the preferred routes between any two computer systems on the interconnected networks.[3]
A router has two types of network element components organized onto separate processing planes:[4]
- Control plane: A router maintains a routing table that lists which route should be used to forward a data packet, and through which physical interface connection. It does this using internal preconfigured directives, called static routes, or by learning routes dynamically using a routing protocol. Static and dynamic routes are stored in the routing table. The control-plane logic then strips non-essential directives from the table and builds a forwarding information base (FIB) to be used by the forwarding plane.
- Forwarding plane: The router forwards data packets between incoming and outgoing interface connections. It forwards them to the correct network type using information that the packet header contains matched to entries in the FIB supplied by the control plane.
Applications[edit]

A typical home or small office DSL router showing the telephone socket (left, white) to connect it to the internet using ADSL, and Ethernet jacks (right, yellow) to connect it to home computers and printers.
A router may have interfaces for different types of physical layer connections, such as copper cables, fiber optic, or wireless transmission. It can also support different network layer transmission standards. Each network interface is used to enable data packets to be forwarded from one transmission system to another. Routers may also be used to connect two or more logical groups of computer devices known as subnets, each with a different network prefix.
Routers may provide connectivity within enterprises, between enterprises and the Internet, or between internet service providers' (ISPs') networks. The largest routers (such as the Cisco CRS-1 or Juniper PTX) interconnect the various ISPs, or may be used in large enterprise networks.[5] Smaller routers usually provide connectivity for typical home and office networks.
All sizes of routers may be found inside enterprises.[6] The most powerful routers are usually found in ISPs, academic and research facilities. Large businesses may also need more powerful routers to cope with ever-increasing demands of intranet data traffic. A hierarchical internetworking model for interconnecting routers in large networks is in common use.[7]
Access, core and distribution[edit]
Access routers, including small office/home office (SOHO) models, are located at home and customer sites such as branch offices that do not need hierarchical routing of their own. Typically, they are optimized for low cost. Some SOHO routers are capable of running alternative free Linux-based firmware like Tomato, OpenWrt or DD-WRT.[8][failed verification]
Distribution routers aggregate traffic from multiple access routers. Distribution routers are often responsible for enforcing quality of service across a wide area network (WAN), so they may have considerable memory installed, multiple WAN interface connections, and substantial onboard data processing routines. They may also provide connectivity to groups of file servers or other external networks.[citation needed]
In enterprises, a core router may provide a collapsed backbone interconnecting the distribution tier routers from multiple buildings of a campus, or large enterprise locations. They tend to be optimized for high bandwidth, but lack some of the features of edge routers.[9][failed verification]
Security[edit]
External networks must be carefully considered as part of the overall security strategy of the local network. A router may include a firewall, VPN handling, and other security functions, or these may be handled by separate devices. Routers also commonly perform network address translation which restricts connections initiated from external connections but is not recognised as a security feature by all experts.[10] Some experts argue that open source routers are more secure and reliable than closed source routers because open source routers allow mistakes to be quickly found and corrected.[11]
Routing different networks[edit]
Routers are also often distinguished on the basis of the network in which they operate. A router in a local area network (LAN) of a single organisation is called an interior router. A router that is operated in the Internet backbone is described as exterior router. While a router that connects a LAN with the Internet or a wide area network (WAN) is called a border router, or gateway router.[12]
Internet connectivity and internal use[edit]
Routers intended for ISP and major enterprise connectivity usually exchange routing information using the Border Gateway Protocol (BGP). RFC 4098 defines the types of BGP routers according to their functions:[13]
- Edge router (also called a provider edge router): Placed at the edge of an ISP network. The router uses Exterior Border Gateway Protocol (EBGP) to routers at other ISPs or large enterprise autonomous systems.
- Subscriber edge router (also called a customer edge router): Located at the edge of the subscriber's network, it also uses EBGP to its provider's autonomous system. It is typically used in an (enterprise) organization.
- Inter-provider border router: A BGP router for interconnecting ISPs that maintains BGP sessions with other BGP routers in ISP Autonomous Systems.
- Core router: Resides within an Autonomous System as a back bone to carry traffic between edge routers.[14]
- Within an ISP: In the ISP's Autonomous System, a router uses internal BGP to communicate with other ISP edge routers, other intranet core routers, or the ISP's intranet provider border routers.
- "Internet backbone:" The Internet no longer has a clearly identifiable backbone, unlike its predecessor networks. See default-free zone (DFZ). The major ISPs' system routers make up what could be considered to be the current Internet backbone core.[15] ISPs operate all four types of the BGP routers described here. An ISP "core" router is used to interconnect its edge and border routers. Core routers may also have specialized functions in virtual private networks based on a combination of BGP and Multi-Protocol Label Switching protocols.[16]
- Port forwarding: Routers are also used for port forwarding between private Internet-connected servers.[6]
- Voice/Data/Fax/Video Processing Routers: Commonly referred to as access servers or gateways, these devices are used to route and process voice, data, video and fax traffic on the Internet. Since 2005, most long-distance phone calls have been processed as IP traffic (VOIP) through a voice gateway. Use of access server type routers expanded with the advent of the Internet, first with dial-up access and another resurgence with voice phone service.
- Larger networks commonly use multilayer switches, with layer 3 devices being used to simply interconnect multiple subnets within the same security zone, and higher layer switches when filtering, translation, load balancing or other higher level functions are required, especially between zones.
Historical and technical information[edit]

The first ARPANET router, the Interface Message Processor delivered to UCLA August 30, 1969, and went online October 29, 1969
The concept of an "Interface computer" was first used by Donald Davies for the NPL network in 1966.[17] The Interface Message Processor (IMP), conceived in 1967 for use in the ARPANET, had fundamentally the same functionality as a router does today. The idea for a router (called "gateways" at the time) initially came about through an international group of computer networking researchers called the International Network Working Group (INWG). Set up in 1972 as an informal group to consider the technical issues involved in connecting different networks, it became a subcommittee of the International Federation for Information Processing later that year.[18] These gateway devices were different from most previous packet switching schemes in two ways. First, they connected dissimilar kinds of networks, such as serial lines and local area networks. Second, they were connectionless devices, which had no role in assuring that traffic was delivered reliably, leaving that entirely to the hosts.[c]
The idea was explored in more detail, with the intention to produce a prototype system as part of two contemporaneous programs. One was the initial DARPA-initiated program, which created the TCP/IP architecture in use today.[19] The other was a program at Xerox PARC to explore new networking technologies, which produced the PARC Universal Packet system; due to corporate intellectual property concerns it received little attention outside Xerox for years.[20] Some time after early 1974, the first Xerox routers became operational. The first true IP router was developed by Ginny Strazisar at BBN, as part of that DARPA-initiated effort, during 1975-1976.[21] By the end of 1976, three PDP-11-based routers were in service in the experimental prototype Internet.[22]
The first multiprotocol routers were independently created by staff researchers at MIT and Stanford in 1981; the Stanford router was done by William Yeager, and the MIT one by Noel Chiappa; both were also based on PDP-11s.[23][24][25][26] Virtually all networking now uses TCP/IP, but multiprotocol routers are still manufactured. They were important in the early stages of the growth of computer networking when protocols other than TCP/IP were in use. Modern Internet routers that handle both IPv4 and IPv6 are multiprotocol but are simpler devices than routers processing AppleTalk, DECnet, IP and Xerox protocols.
From the mid-1970s and in the 1980s, general-purpose minicomputers served as routers. Modern high-speed routers are highly specialized computers with extra hardware added to speed both common routing functions, such as packet forwarding, and specialised functions such as IPsec encryption. There is substantial use of Linux and Unix software based machines, running open source routing code, for research and other applications. The Cisco IOS operating system was independently designed. Major router operating systems, such as Junos and NX-OS, are extensively modified versions of Unix software.
Forwarding[edit]
Further information: Routing and IP routing
The main purpose of a router is to connect multiple networks and forward packets destined either for its own networks or other networks. A router is considered a layer-3 device because its primary forwarding decision is based on the information in the layer-3 IP packet, specifically the destination IP address. When a router receives a packet, it searches its routing table to find the best match between the destination IP address of the packet and one of the addresses in the routing table. Once a match is found, the packet is encapsulated in the layer-2 data link frame for the outgoing interface indicated in the table entry. A router typically does not look into the packet payload,[citation needed] but only at the layer-3 addresses to make a forwarding decision, plus optionally other information in the header for hints on, for example, quality of service (QoS). For pure IP forwarding, a router is designed to minimize the state information associated with individual packets.[27] Once a packet is forwarded, the router does not retain any historical information about the packet.[d]
The routing table itself can contain information derived from a variety of sources, such as a default or static routes that are configured manually, or dynamic routing protocols where the router learns routes from other routers. A default route is one that is used to route all traffic whose destination does not otherwise appear in the routing table; this is common – even necessary – in small networks, such as a home or small business where the default route simply sends all non-local traffic to the Internet service provider. The default route can be manually configured (as a static route), or learned by dynamic routing protocols, or be obtained by DHCP.[e][28]
A router can run more than one routing protocol at a time, particularly if it serves as an autonomous system border router between parts of a network that run different routing protocols; if it does so, then redistribution may be used (usually selectively) to share information between the different protocols running on the same router.[29]
Besides making a decision as to which interface a packet is forwarded to, which is handled primarily via the routing table, a router also has to manage congestion when packets arrive at a rate higher than the router can process. Three policies commonly used in the Internet are tail drop, random early detection (RED), and weighted random early detection (WRED). Tail drop is the simplest and most easily implemented; the router simply drops new incoming packets once the length of the queue exceeds the size of the buffers in the router. RED probabilistically drops datagrams early when the queue exceeds a pre-configured portion of the buffer, until a pre-determined max, when it becomes tail drop. WRED requires a weight on the average queue size to act upon when the traffic is about to exceed the pre-configured size, so that short bursts will not trigger random drops.[citation needed]
Another function a router performs is to decide which packet should be processed first when multiple queues exist. This is managed through QoS, which is critical when Voice over IP is deployed, so as not to introduce excessive latency.[citation needed]
Yet another function a router performs is called policy-based routing where special rules are constructed to override the rules derived from the routing table when a packet forwarding decision is made.[30]
Router functions may be performed through the same internal paths that the packets travel inside the router. Some of the functions may be performed through an application-specific integrated circuit (ASIC) to avoid overhead of scheduling CPU time to process the packets. Others may have to be performed through the CPU as these packets need special attention that cannot be handled by an ASIC.[citation needed]
See also[edit]
- DECbit
- Mobile broadband modem
- Modem
- Residential gateway
- Switch virtual interface
- TCAM Content addressable memory (hardware acceleration of route-search)
- Wireless router
Notes[edit]
- ^ Router is pronounced /ˈruːtər/ in British English and is pronounced /ˈraʊtər/ in American and Australian English.[1]
- ^ As opposed to a network switch, which connects data lines from one single network
- ^ This particular idea had been previously pioneered in the CYCLADES network.
- ^ The forwarding action can be collected into the statistical data, if so configured.
- ^ A router can serve as a DHCP client or as a DHCP server.
References[edit]
- ^ "router". Oxford English Dictionary (3rd ed.). Oxford University Press. September 2005. (Subscription or UK public library membership required.)
- ^ "Overview Of Key Routing Protocol Concepts: Architectures, Protocol Types, Algorithms and Metrics". Tcpipguide.com. Archived from the original on 20 December 2010. Retrieved 15 January 2011.
- ^ "Cisco Networking Academy's Introduction to Routing Dynamically". Cisco. Archived from the original on October 27, 2015. Retrieved August 1, 2015.
- ^ H. Khosravi & T. Anderson (November 2003). Requirements for Separation of IP Control and Forwarding. doi:10.17487/RFC3654. RFC 3654.
- ^ "Setting uo Netflow on Cisco Routers". MY-Technet.com date unknown. Archived from the original on 14 July 2011. Retrieved 15 January 2011.
- ^ Jump up to:a b "Windows Home Server: Router Setup". Microsoft Technet 14 Aug 2010. Archived from the original on 22 December 2010. Retrieved 15 January 2011.
- ^ Oppenheimer, Pr (2004). Top-Down Network Design. Indianapolis: Cisco Press. ISBN 978-1-58705-152-4.
- ^ "Windows Small Business Server 2008: Router Setup". Microsoft Technet Nov 2010. Archived from the original on 30 December 2010. Retrieved 15 January 2011.
- ^ "Core Network Planning". Microsoft Technet May 28, 2009. Archived from the original on 2 October 2010. Retrieved 15 January 2011.
- ^ "Security Considerations Of NAT" (PDF). University of Michigan. Archived from the original (PDF) on October 18, 2014.
- ^ "Global Internet Experts Reveal Plan for More Secure, Reliable Wi-Fi Routers - and Internet". Archived from the original on 2015-10-20.
- ^ Tamara Dean (2009). Network+ Guide to Networks. Cengage Learning. p. 272. ISBN 9781423902454.
- ^ H. Berkowitz; et al. (June 2005). Terminology for Benchmarking BGP Device Convergence in the Control Plane. doi:10.17487/RFC4098. RFC 4098.
- ^ "M160 Internet Backbone Router" (PDF). Juniper Networks. Archived (PDF) from the original on 20 September 2011. Retrieved 15 January 2011.
- ^ "Virtual Backbone Routers" (PDF). IronBridge Networks, Inc. September, 2000. Archived (PDF) from the original on 16 July 2011. Retrieved 15 January 2011.
- ^ BGP/MPLS VPNs,RFC 2547, E. Rosen and Y. Rekhter, April 2004
- ^ Roberts, Dr. Lawrence G. (May 1995). "The ARPANET & Computer Networks". Archived from the original on 24 March 2016. Retrieved 13 April 2016.
Then in June 1966, Davies wrote a second internal paper, "Proposal for a Digital Communication Network" In which he coined the word packet,- a small sub part of the message the user wants to send, and also introduced the concept of an "Interface computer" to sit between the user equipment and the packet network.
- ^ Davies, Shanks, Heart, Barker, Despres, Detwiler and Riml, "Report of Subgroup 1 on Communication System", INWG Note No. 1.
- ^ Vinton Cerf, Robert Kahn, "A Protocol for Packet Network Intercommunication", IEEE Transactions on Communications, Volume 22, Issue 5, May 1974, pp. 637 - 648.
- ^ David Boggs, John Shoch, Edward Taft, Robert Metcalfe, "Pup: An Internetwork Architecture" Archived 2008-09-11 at the Wayback Machine, IEEE Transactions on Communications, Volume 28, Issue 4, April 1980, pp. 612- 624.
- ^ "Ms. Ginny Strazisar". IT History Society. Archivedfrom the original on 1 December 2017. Retrieved 21 November 2017.
- ^ Craig Partridge, S. Blumenthal, "Data networking at BBN"; IEEE Annals of the History of Computing, Volume 28, Issue 1; January–March 2006.
- ^ Valley of the Nerds: Who Really Invented the Multiprotocol Router, and Why Should We Care? Archived 2016-03-03 at the Wayback Machine, Public Broadcasting Service, Accessed August 11, 2007.
- ^ Router Man Archived 2013-06-05 at the Wayback Machine, NetworkWorld, Accessed June 22, 2007.
- ^ David D. Clark, "M.I.T. Campus Network Implementation", CCNG-2, Campus Computer Network Group, M.I.T., Cambridge, 1982; pp. 26.
- ^ Pete Carey, "A Start-Up's True Tale: Often-told story of Cisco's launch leaves out the drama, intrigue", San Jose Mercury News, December 1, 2001.
- ^ Roberts, Lawrence (22 July 2003). "The Next Generation of IP - Flow Routing". Archived from the original on 4 April 2015. Retrieved 22 February 2015.
- ^ David Davis (April 19, 2007). "Cisco administration 101: What you need to know about default routes". Archivedfrom the original on December 19, 2017.
- ^ Diane Teare (March 2013). Implementing Cisco IP Routing (ROUTE): Foundation Learning Guide. Cisco Press. pp. 330–334.
- ^ Diane Teare (March 2013). "Chapter 5: Implementing Path Control". Implementing Cisco IP Routing (ROUTE): Foundation Learning Guide. Cisco Press. pp. 330–334.
External links[edit]
| Wikimedia Commons has media related to Network routers. |
| Wikibooks has a book on the topic of: Communication Networks/Routing |
| Look up router in Wiktionary, the free dictionary. |
- Internet Engineering Task Force, the Routing Area last checked 21 January 2011.
| hide | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Operating systems/ Network operating systems |
| ||||||||||||||
| Routing daemons | |||||||||||||||
| Other software | |||||||||||||||
| Related articles | |||||||||||||||
Subscribe to:
Comments (Atom)